The problem with simple passwords
Long before word processing, spreadsheets, and most recently AI, modern computers were designed to do math quickly. In 1965, Intel CEO Gordon Moore observed that every year the number of components per integrated circuit doubled. In 1975, this number was revised, doubling every two years. This has held true for every year from 1975 on. This is known as “Moore’s Law.“
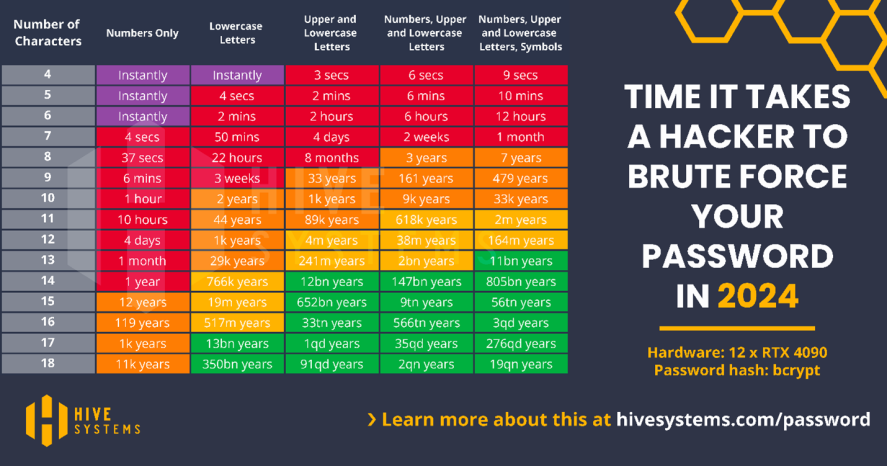
Cracking a password comes down to a math problem. The featured table above shows recent statistics for password cracking using hardware commonly found in desktop computers based on complexity.
This highlights that using more characters and requiring numbers, upper- and lower-case letters and symbols makes it significantly harder to crack a password. It is why accounts are set to lock out after number of password attempts.
Part of password complexity includes lock out triggers and lock out times. It is unlikely a user will type a password incorrectly five times and even less likely to do so in one second. Requiring a 15 minute time out after five consecutive incorrect password attempts increases the amount of time required to crack a password.
According to a Forbes study, 35% of people with stolen passwords say that a simple password was the cause of their problems.
The problem with reusing passwords
People come up with a single password they are comfortable with.
Seventy-eight percent reuse passwords and 68% who had their password stolen have to change it in multiple places.
The problem with using a single factor
What is a factor when it comes to multifactor authentication. A factor is a piece of evidence to get a computer, a network or an application to trust a user with information or privileges. Factors are broken out into three categories:
- Something you have. Examples include physical keys, a car fob, a badge, a bank card, a phone, a USB token.
- Something you know. Examples include a password, social security number, date of birth, mother’s maiden name.
- Something you are. Examples include facial recognition, voice recognition, fingerprints, eye iris recognition.
From the Forbes study, 27% of credentials were exposed due to a company data breach and 21% were stolen through phishing attacks.
Looking at the combination of cracked passwords, passwords that are guessed because of reuse, or passwords that are stolen, the value of additional factors becomes easy to see. This is why you need a PIN to access your bank account with your card.